Why Your Digital Presence Needs a Fortress
High-security hosting is a specialized service that implements robust measures to protect websites from cyber threats. It goes beyond standard hosting by providing advanced threat protection (WAF, DDoS mitigation), proactive 24/7 monitoring, isolated infrastructure, compliance support (GDPR, PCI DSS), and automated disaster recovery backups.
With a cyberattack occurring every 39 seconds, according to a University of Maryland study, this isn’t a hypothetical threat—it’s a daily reality. A single data breach can lead to lost customer trust, legal liabilities, revenue loss, and severe SEO penalties from Google. Many businesses focus on design and marketing but neglect the security foundation, like building a storefront with no locks.
Outdated software is a primary vulnerability; in 2019, 60% of infected CMS applications were out of date. High-security hosting ensures your site stays online, customer data remains protected, and your reputation stays intact. It’s the difference between weathering an attack and becoming another statistic.
I’m Magee Clegg, founder and CEO of Cleartail Marketing. Since 2014, we’ve helped over 90 B2B companies build and protect their online presence. We know that a secure foundation is crucial for digital growth, which is why we prioritize it for every client before driving traffic to their site.
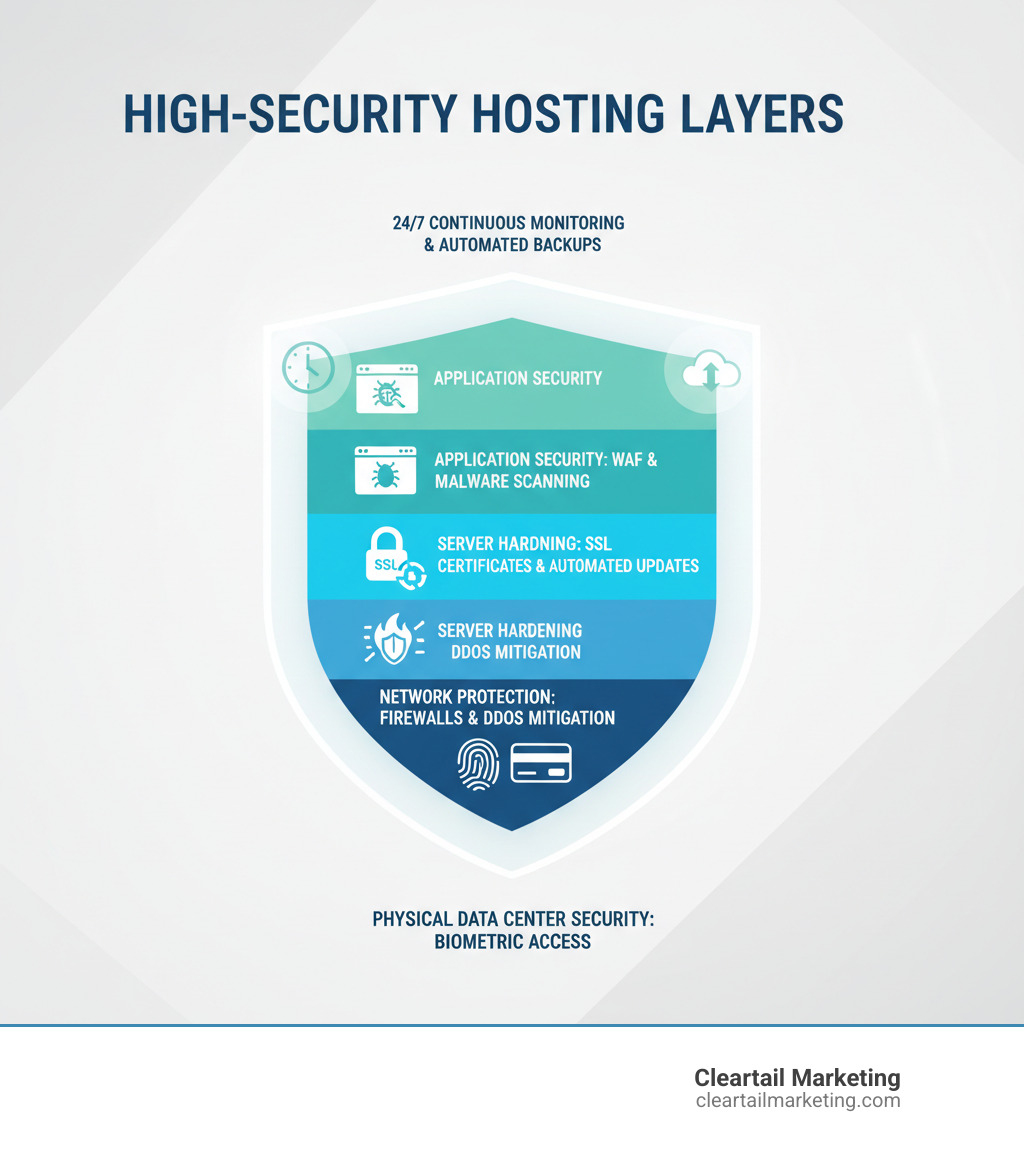
The Core Components of a Secure Hosting Environment
Think of high-security hosting like a bank vault for your website—it requires multiple layers of protection working in unison. A secure website is built on several core components that form a unified defense system.
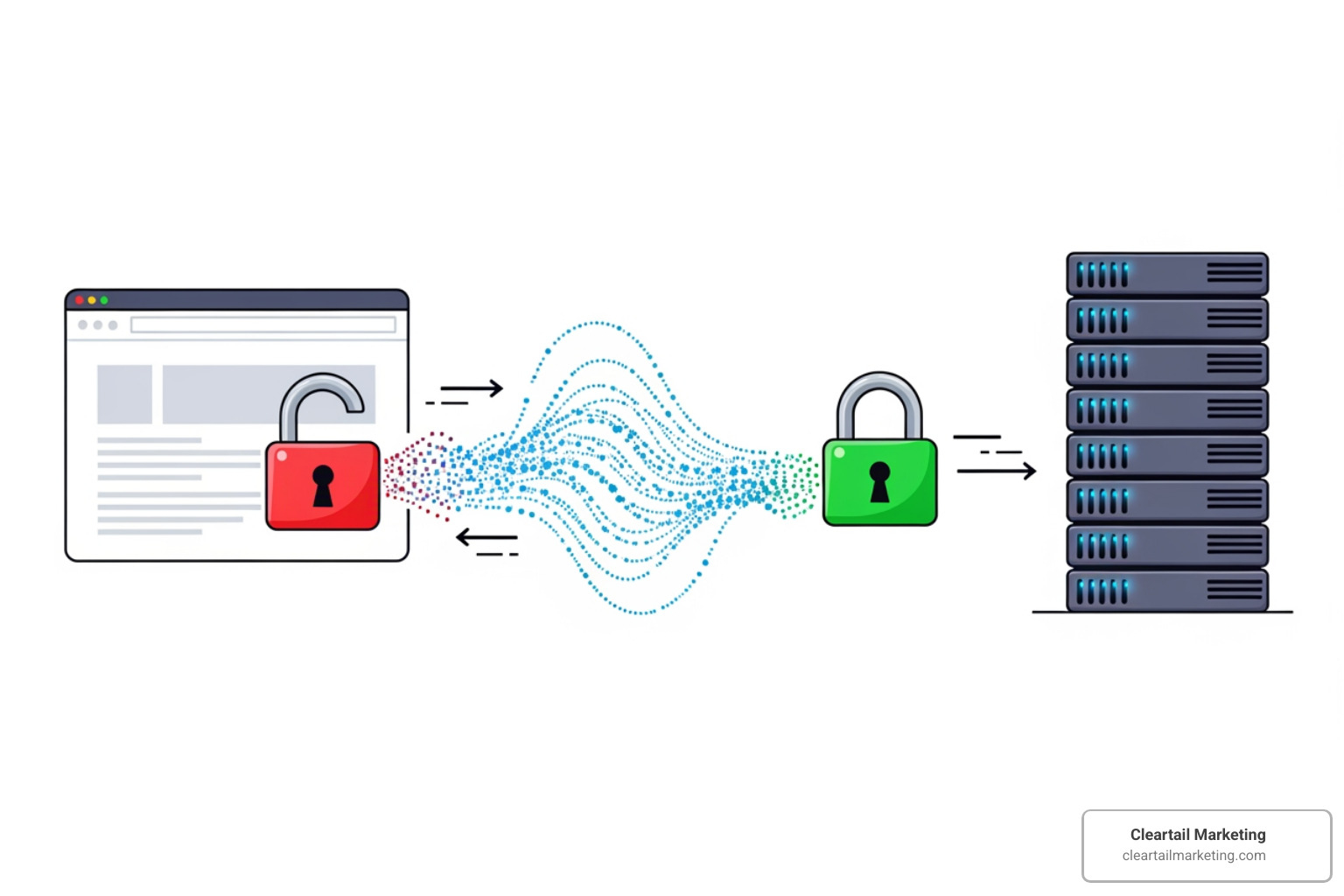
-
SSL Certificates: This is your first line of defense, encrypting all data—credentials, credit card numbers, form submissions—traveling between a visitor’s browser and your server. Without SSL, data is vulnerable. With it, the information is unreadable to outsiders. Google also penalizes sites without SSL certification, making it essential for both security and SEO.
-
Web Application Firewalls (WAFs): A WAF acts as your website’s bouncer, inspecting incoming traffic and blocking malicious requests like SQL injections and cross-site scripting (XSS) before they reach your application. While a network firewall protects the server, a WAF specifically guards your website’s software.
-
DDoS Protection: A Distributed Denial-of-Service (DDoS) attack floods your site with fake traffic, overwhelming the server and blocking real customers. Quality hosts use DDoS mitigation to identify and filter these malicious traffic surges, ensuring your site stays online for legitimate visitors.
-
Malware Scanning and Removal: This works like an immune system, proactively scanning for infections and quarantining threats before they can spread, steal data, or take over your site. The system isolates infected files, cleans them, or removes them automatically, preventing viruses and spyware from taking hold.
-
Automated Backups: Backups are your time machine for disaster recovery. Whether facing a hack, a bad update, or human error, automated daily backups allow you to restore your site to a working state quickly. They are your ultimate safety net when other defenses fail.
-
24/7 Monitoring: The best hosts check server health constantly—some as often as every 0.5 seconds. This surveillance catches issues early, often before they affect visitors, turning potential floods into manageable leaks.
These elements form the foundation of a secure digital presence. SSL builds trust and improves search rankings, firewalls proactively block attacks, and backups ensure you can recover from any incident. At Cleartail Marketing, we integrate these protections into every project from the start. Security isn’t an add-on; it’s part of the architecture. You can see this approach in our WordPress Website Design and Development services. To learn more about building resilient websites, check out our approach to Website Design and Development.
Comparing Hosting Types: A Security Perspective
Choosing a hosting type is a critical security decision. The right choice depends on your needs for isolation (separation from other sites), resource control, and customizability. Think of it like choosing between a shared apartment, a private condo, or a standalone house—each offers different levels of protection.

Shared vs. Dedicated: A Tale of Two Security Models
Shared hosting is the most affordable option, where your site shares server resources with hundreds of others. The main security risk is the “bad neighbor” effect: a vulnerability on one site can potentially be exploited to access others on the same server, a risk known as cross-site contamination. While reputable providers like Hostinger offer server-level security, you have limited control and cannot implement custom configurations.
Dedicated hosting provides an entire physical server exclusively for your website, eliminating the risk of cross-site contamination. You get full server control to install specialized security software and create custom configurations, which is ideal for e-commerce sites or businesses with strict compliance needs. Providers like GreenGeeks offer dedicated plans for maximum control, though this comes at a higher cost and with more management responsibility. To understand how these choices affect your budget, explore different Website Hosting Costs.
Is Cloud or VPS Hosting the Right Choice for Security?
For many businesses, Virtual Private Servers (VPS) and Cloud Hosting offer a strong balance of security and affordability.
A VPS divides a physical server into isolated virtual machines. A hypervisor ensures that a security breach on one VPS cannot affect yours. You get dedicated resources and root access, allowing for custom security tools not possible on shared hosting. This dramatically reduces the “bad neighbor” risk at a reasonable cost. Liquid Web, for example, offers VPS hosting with integrated firewalls and DDoS protection.
Cloud hosting distributes your website across a network of interconnected servers. This provides exceptional redundancy and scalability; if one server fails or is attacked, another takes over seamlessly. This distributed nature makes it harder for attackers to find a single point of failure. Cloud providers like OVHcloud also offer geographic distribution and “Trusted Zones” to meet data residency requirements, while Hostinger’s cloud plans provide improved security and performance. For most businesses needing high-security hosting, VPS and cloud options strike the best balance. If you’re trying to decide, compare Hosting Plans to find your fit and align the hosting type with your security needs.
Beyond the Basics: Advanced vs. Standard Security Measures
Not all “secure hosting” is equal. Standard security covers the basics like a free SSL certificate, a simple network firewall, and daily backups. While important, this is like locking your front door but leaving the windows open. Some hosts like Ionos include malware scanning, but it’s often reactive.
Advanced security, the hallmark of high-security hosting, is proactive. It doesn’t just respond to threatsit anticipates and neutralizes them before they can cause damage.
The Power of Proactive High-Security Hosting
Proactive security uses advanced tools to stay ahead of attackers:
-
AI-Powered Protection: Artificial intelligence analyzes traffic in real-time to identify and block threats that traditional methods miss. For instance, SiteGround’s AI blocks millions of brute-force login attempts daily, and Hostinger’s AI tools like Kodee can help with security oversight.
-
Real-Time Monitoring & Automated Response: Top hosts monitor servers constantly (SiteGround checks every 0.5 seconds). When an issue is detected, the system responds immediately by blocking malicious IPs or quarantining suspicious files, without waiting for human intervention.
-
Managed WAF and Intrusion Detection: A managed Web Application Firewall (WAF), often combined with Intrusion Detection/Prevention Systems (IDS/IPS), is updated by experts to defend against the latest attack vectors. This provides a round-the-clock defense for your applications.
-
Server Hardening & Proactive Patching: Hardening involves minimizing the attack surface by disabling non-essential services. Proactive patching addresses a huge vulnerability: outdated software. High-security hosts automatically apply OS and security updates, so you’re not left exposed. This proactive approach is vital for protecting your revenue and reputation. A secure foundation is also key for lasting results from our Search Engine Optimization Agency services.
Data Privacy, Compliance, and Your Host
Your hosting provider is a key partner in meeting legal data privacy obligations. Choosing the wrong one can lead to serious financial and legal trouble.
-
Regulatory Compliance: If you handle customer data, compliance with regulations like GDPR (for EU customers), HIPAA (for healthcare data), and PCI DSS (for credit card payments) is mandatory. Look for hosts that explicitly support these standards and operate highly secure data centers validated by independent certifications such as ISO/IEC 27001 and PCI DSS.
-
Physical Data Center Security: Your data lives in physical buildings that need protection. Top-tier data centers feature biometric scanners, 24/7 surveillance, and redundant power and cooling. Switzerland’s Infomaniak, for instance, operates TIER III+ data centers with extreme security measures.
-
Data Residency and Sovereignty: Where your data is stored determines which laws govern it. Some regulations require data to remain within specific borders. OVHcloud’s “Trusted Zones” keep data within the EU, protecting it from non-EU laws. Look for hosts with independent compliance certifications like ISO 27001 or SOC 2 to verify their security standards. A strong commitment to privacy builds customer trust and protects your brand. Discover our Reputation Management services to see how we help businesses protect their online standing.
Your Role in the Security Partnership: A Website Owner’s Checklist
High-security hosting is a powerful defense, but it’s a partnership. Your host secures the server and network infrastructure, but you are responsible for what happens at the application level—your software, passwords, and user permissions. Your host builds the fortress, but you control who has the keys.
Essential Security Practices for Website Owners
To uphold your end of the security partnership, follow these essential practices:
-
Use Strong, Unique Passwords and 2FA: Weak passwords are a top vulnerability. Use a password manager to generate complex, unique passwords for every account. More importantly, enable Two-Factor Authentication (2FA) wherever possible to add a critical layer of protection.
-
Keep All Software Updated: This is the single most important thing you can do. Hackers exploit known vulnerabilities in outdated software. Promptly update your CMS core (like WordPress), plugins, and themes. Enable automatic updates for minor security patches.
-
Limit User Privileges: Follow the principle of least privilege. Give users the minimum access level they need to perform their jobs. If a limited-access account is compromised, the potential damage is contained.
-
Use a Reputable Security Plugin: For CMS sites like WordPress, a security plugin (e.g., Wordfence, Sucuri) adds application-level defense with malware scanning, a firewall, and login attempt limiting.
-
Be Wary of Phishing Scams: Phishing emails trick you into revealing sensitive information. Be suspicious of any unsolicited email asking for credentials. Verify the sender and avoid clicking suspicious links. As Google notes, phishing can involve everything from sharing passwords to downloading malicious software.
-
Perform Regular Client-Side Backups: While your host provides backups, having your own independent copies stored off-site gives you complete control over disaster recovery. It’s your ultimate insurance policy.
Red Flags: Signs of Insecure Hosting to Avoid
Recognizing the signs of poor hosting is just as important as knowing what to look for:
- No free SSL: In 2024, SSL is a basic security and SEO requirement. Hosts that charge for it are behind the times.
- Outdated PHP versions: Running old, unsupported PHP versions exposes your site to known vulnerabilities.
- Poor customer reviews on security: Check sites like Trustpilot and the Better Business Bureau for patterns of security complaints.
- Lack of transparency: A good host is proud of its security infrastructure and will discuss it openly. Vague answers are a major red flag.
- Frequent downtime: This can indicate unstable servers, poor maintenance, or an inability to handle attacks.
- Slow support for security issues: When a breach occurs, every minute counts. A slow or unhelpful support team can turn a small problem into a catastrophe.
Cheap hosting often becomes the most expensive choice after a security breach. A secure website is also crucial for protecting the search engine rankings you’ve worked to build. Learn how to do SEO to protect your rankings and maintain your online visibility.
Conclusion: Fortify Your Future with Secure Hosting
With a cyberattack happening every 39 seconds, website security is no longer optional. High-security hosting has become essential for any business that values its reputation, customers, and revenue.
A truly secure environment is built on fundamentals like SSL encryption, Web Application Firewalls, and DDoS protection, layered with proactive malware scanning, automated backups, and 24/7 monitoring. Your choice of hosting—whether shared, VPS, cloud, or dedicated—also plays a critical role in your overall security posture.
High-security hosting is about more than preventing attacks. It’s about protecting your customer relationships, brand reputation, search rankings, and revenue. A single breach can undo years of hard work, but with the right hosting partner and good security practices, this is a preventable nightmare.
At Cleartail Marketing, we’ve spent a decade helping businesses build digital presences that are not just effective but also safe and resilient. We know that security is the foundation upon which all digital marketing success is built.
Security is an investment in your future. By taking it seriously from day one, you can save yourself from catastrophic losses down the road. Ready to build your website on a foundation you can trust? Compare hosting plans with us to find the perfect fortress for your website and ensure your online presence is built to last.



